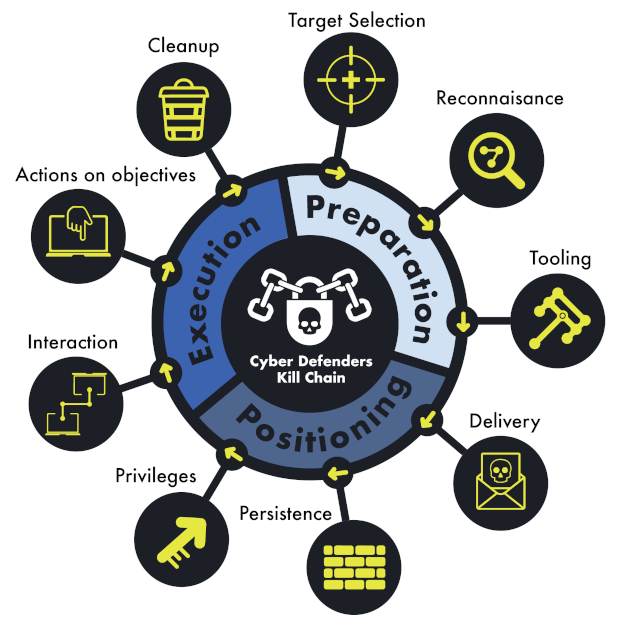
The Cyber Defenders Kill Chain (TCDO Part2)
Getting domain admin is not “game over”, it's merely a phase of an adversary's positioning activities. It's the things that happen after that which could well mean game over.
If you do not know what the goals of an adversary are, then you neither know what positioning they need to achieve, nor what they will do once they achieve that positioning. Subsequently, if you don't know what would cause irreparable damage to your organisation, then you cannot defend against it.
To assume that an adversary requires a high level of privileges in order to execute their attack is usually a sign that an adversary's motives within an organisation are not well understood. Preventing those privileges being obtained is not a terrible thing as long as it is mindful of the fact that an adversary probably doesn't need to traverse the path that provides them these privileges at all. To ensure that tailored cyber defences are as effective (and simple) as they can be we created our own cyber defenders kill chain and we’ll cover some of the thinking that led to its creation in this short article:
Lab539 Cyber Defenders Kill Chain
A while ago we posted an article about "Applying Context, Controlling Adversaries" which talked about how context is vital in crafting effective cyber defences and how this can enable you to dictate how an adversary must operate, rather than having to defend against all possibilities (https://www.lab539.com/blog/applying-context-to-control-adversaries-part1)
To apply context, we typically start at the end - in the sense that we want to start by understanding the thing(s) that would fundamentally undermine an organisation's ability to operate. Gaining admin rights is not one of those things. Compromising critical systems is also not one of those things. Both could well be part of that journey, but they are ‘positioning activities’, not execution. Focusing cyber defence programs entirely around preventing positioning activities is an excellent way to make cyber defence an IT problem, rather than a business risk problem. Your organisation has admins, and it has people who have access to critical systems, yet it still functions. So, neither of those alone have fundamentally undermined your ability to operate as a business, but they might enable an adversary to do so.
Cyber defence programs need to lead with preventing events which have a significant impact on an organisation from occurring. If cyber defence programs lead with preventing positioning activities from occurring, they will not resonate outside of IT and, because they are focused on solving what is usually an impossible and ongoing challenge, they will also not succeed.
Preventing positioning is usually a scale problem, there may be an infinite number of ways to achieve positioning which means covering them all can be impossible, no matter how much tooling you invest in. Execution, however, is usually the opposite, it's not a scale problem but a context one. If you don't have context then it's impossible, but with context often the scale reduces to single digits, sometimes even down to a single option. It's much easier to control a single activity occurring than it is to control an infinite number of positioning activities. It's why, when crafting tailored cyber defences, context is essential and is why, in our cyber defenders kill chain, we ensure that the execution phase is well represented as a place where high fidelity controls can be introduced rather than it being seen as the doomsday moment occurring. It is also why we start at the end and work our way backwards when crafting tailored cyber defences.
We find our cyber defenders kill chain useful because it works with the ways that we craft tailored cyber defences. If it resonates with you then please feel free to use and share this work under a Creative Commons Attribution-ShareAlike (CC BY-SA) License. You’re also welcome to remove any Lab539 branding, just give a reference to Lab539 when you do! https://creativecommons.org/licenses/by-sa/4.0/