Cyber Security, Fuel Terminals and Operational Networks
In late January 2022, a series of cyber-attacks hit oil distribution terminals in Europe affecting the Marquard and Bahls owned companies OilTanking GmbH and Mabanaft GmbH. OilTanking declared a force majeure and Mabanaft also did the same for most of their inland activities within Germany.
Around the same time SEA-invest's largest terminal in Antwerp (SEA-Tank) and one of Evos’ terminals in Amsterdam were also hit by incidents which affected loading and unloading.
This all occurred whist tensions were particularly high between Russia and Ukraine and whilst the rest of Europe are being incredibly careful not to be the be the one that results in things escalating. Holland’s NCSC (National Cyber Security Centre) has stated that the attacks do not appear to be related to the invasion of Ukraine which occurred several weeks later; that they were entirely financially motivated and not coordinated.
Whilst no affected organization has shared extensive details on their incidents, what we do know is that these were cyber extortion (ransomware) attacks. An internal report from the Federal Office for Information Security (BSI), obtained by the German newspaper Handelsblatt, identified the BlackCat ransomware group as being behind the attacks on the two German oil companies which ended up affecting hundreds of gas stations across northern Germany.
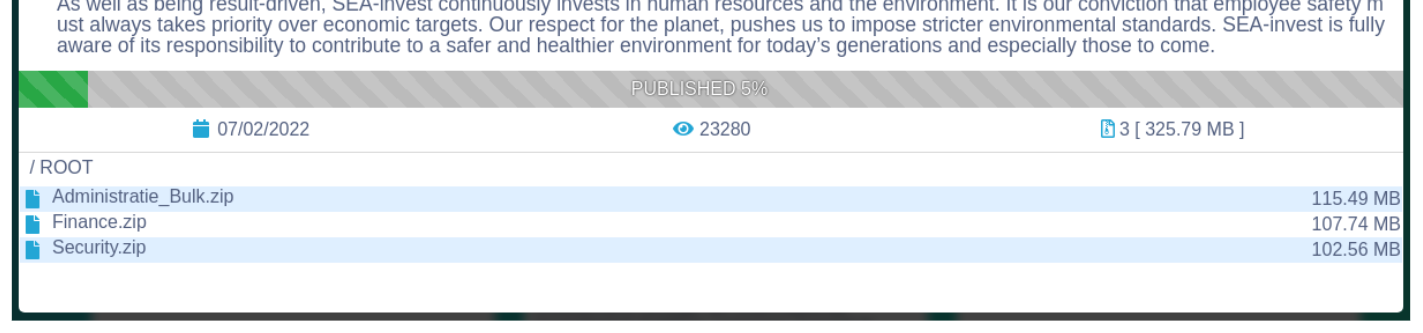
We know that Conti were behind the Sea-Invest attacks because they posted information on their website and leaked a proportion of the data they had pulled from their victim:
More recently, in July 2023, the Canadian Centre for Cyber Security published a document on “The Cyber Threat to Canada's Oil and Gas Sector”. This paper made several key judgements summarized below:
Financially motivated cybercrime, particularly Business Email Compromise (BEC) and ransomware are almost certainly the main cyber threats facing the Canadian oil and gas sector.
Ransomware is almost certainly the primary cyber threat to the reliable supply of oil and gas to Canadians.
The oil and gas sector in Canada will continue to be targeted by state-sponsored cyber espionage.
The oil and gas sector is a strategic target for state sponsored cyber activity.
The primary target is likely Operational Technology (OT) networks.
It is very unlikely that a state-sponsored cyber-attack would intentionally disrupt or damage oil and gas infrastructure outside of hostilities.
This paper was published on 21st June and written based upon assessments and analysis available as of 31st March 2023. The paper was certainly very timely, as on 25th June 2023 Suncor Energy, a major player in Canada’s oil and gas space, was hit by a cyber security incident which resulted in gas stations across Canada facing problems.
Whilst Suncor have chosen not to share further details on the incident, many reports highlight disruption to the Petro Canada (a subsidiary of Suncor) Petro-Points scheme as well as to customers' ability to make payments. It does hold the hallmarks of a ransomware incident, but the timing also coincided with an uptick in activity relating to a historical targeting of Suncor which occurred in 2018. This campaign saw quite targeted activities impersonating the Suncor HR (Human Resources) website and enticing users to complete a document containing malicious macros. Hopefully this resurgence in activity is coincidental and not an indication that the breach was the result of a 5 year old campaign remaining undetected and resident. Whatever the case, it certainly serves as a reminder on the persistence of the threat.
A couple of weeks after Suncor’s incident, in July 2023, America’s Cybersecurity and Infrastructure Security Agency (CISA) advised of vulnerabilities (the most significant of which being CVE-2023-3595) affecting Rockwell automation Allen-Bradley ControlLogix systems. What was particularly interesting here was that the vulnerability was identified as a result of it being discovered in a toolkit of an Advanced Persistent Threat (APT). Unusually, there was also high confidence that this toolkit had not been used.
CISA worked with a small number of US firms as well as Rockwell to do the analysis and shared some detailed detections which defenders protecting organizations using Rockwell kit could utilize in their defenses. This work spanned a couple of weeks and meant that when the vulnerability was announced publicly patches, detection signatures, and a wealth of other detail were immediately available to those affected.
Whilst we’ll never know for sure where the exploit was recovered from, likelihood is that it was recovered from one of the following; a live incident, an exploit broker, or having been burned/intercepted in offensive operations and so disclosed via CISA to reduce future exploit potential.
The vulnerabilities disclosed were present in the Rockwell implementation of the Common Industrial Protocol (CIP) on several models of their devices. It is very unlikely that a vulnerability like this would have been stumbled upon, suggesting a level of work, research, and targeting has taken place. The choice of protocol in which the vulnerabilities lie means that it is something unlikely to be subject to effective security monitoring in most environments, thus exploitation would almost certainly be a very stealthy and undetected event.
The APT in possession of this exploit is unlikely, now that this has been disclosed, to simply down tools and give up targeting operational technology. It leaves us with an uncomfortable conclusion that there are, unquestionably, APTs out there who are deeply knowledgeable of, and have access to, the technologies used in the oil and gas space. We can also be confident that they have invested time and effort in targeting these technologies in a manner which supports their stealth ambitions and evades typical defensive approaches which rely on known bads.
The above only scratches the surface of some of the cyber activity that has been going on in this space in the last couple of years. The examples we have shared highlight the sheer range and capabilities encompassed within the threats the industry faces. Everything from opportunist cyber extortion all the way to highly capable and state sponsored APTs. As a key part of critical national infrastructure, defending from these threats is essential, but is far from a trivial task and achieving it effectively does rely on a well thought out approach.
The Threat
As the Canadian Centre for Cyber Security highlight, despite some certainty that state sponsored actors are targeting this sector, a disruptive attack outside of hostilities is considered unlikely. The UK’s NCSC has also made similar statements with regards the risk to the UK when commenting on operational environments.
It is probable that these statements hold true elsewhere, not just within the UK and Canada. However, not all countries are fortunate enough to be, or remain, outside of hostilities – whether this be politically motivated such as the drivers behind the recent (July 2023) attacks on the BAZAN group’s Haifa Bay petrochemical facilities which resulted in access to SCADA terminals and PLC programming interfaces being gained. Or whether this be a sophisticated and targeted state sponsored offensives with intent to disrupt, as we have seen being levied towards Ukraine.
Recently CISA Director Jen Easterly warned that the Chinese Government is likely getting itself into the position to conduct disruptive attacks on American pipelines, railroads and other critical infrastructure if the US gets involved during a potential invasion of Taiwan. Reports also show a move in the Iranian hacker groups APT33’s activities towards OT (Operational Technology) and ICS (Industrial Control Systems). It is likely that their focus will be predominantly focused on Israel, the Gulf States as well as the US and several other European countries.
The more generic attacks, such as cyber extortion (ransomware) remain as prevalent as ever, with incidents like Cl0p’s MOVEit campaign earlier this year proving that no organization or sector is off the table.
Whilst OT networks are being increasingly targeted, it is still true that most incidents which have affected operations at facilities are still primarily IT incidents. The knock-on impact on operations is usually the result of systems which sit between IT and OT environments being affected, or because of safety measures being employed which shut things down to ensure no further impact. Protecting OT networks (and those which bridge IT and OT) is a topic which is becoming increasingly important and one the rest of this article focuses on.
The Response
It wouldn’t be accurate to say that OT environments are not complex but, compared to an IT environment, they are at least somewhat predictable. In an OT environment your PLC doesn’t suddenly choose to check their personal email, sign up to that new SaaS platform or click through and open the Excel spreadsheet they just received whilst working from a coffee shop. In an OT environment how systems operate is mostly deterministic and this falls heavily in the defenders' favor, so we can, and should, take advantage of this in our defenses.
The home advantage is something which we can leverage too. If you know how an adversary would target your organization and what their goal would be then you can simply overlay that onto your environment and build some tailored defenses to protect them. Tooling may support aspects of this, but defenses should not be tooling led. Most tooling led defenses focus on detecting and defending all known knowns, but without context they are unable to defend and detect more complex operations and usually result in an unmanageable amount of noise. We also know (from the earlier Rockwell example) that there are an awful lot of unknowns and unexplored technology in OT environments which means, even if you ignore the lack of context, there will be gaps in the tooling's visibility. Good tooling might be able to signature firmware updates being pushed to a device, but it will be unable to tell you when someone is modifying your blending recipes on your TAS (Terminal Automation System), or when access controls to a facility are being manipulated without some tailoring. This tailoring is context that you will need to provide if you want to prevent adversaries carrying out their actions on objectives, rather than merely increasing the complexity of their positioning phase. Hence, securing these environments requires the right balance of people and technology.
If this sounds complex, then it is likely that you have a lack of visibility over what exists, what is going on within your OT network, and how it is functioning. Lack of visibility is the number one reason Lab539 sees overspend when it comes to cyber security (a belief that tooling will fill the gaps). Visibility isn’t simply about asset inventories, it is about understanding how an entire process works, including what talks to what and how, and it can often be captured with surprising ease in OT environments.
By gaining this visibility, you can tailor defenses to protect a process in a highly accurate and high-fidelity manner without all the noise and triage that are far too common in many cyber security approaches. Confidence that your environment knows what an attack on it looks like and can defend itself from such an attack means that your engineers can spend their time using the environment for what it was intended, rather than being bogged down moonlighting as cyber security practitioners. It has an added benefit in that if you have identified the events you don’t wish to occur then you can plan and pre-authorize aspects of the response too. Meaning you can have playbooks ready and no need to make critical decisions on the fly amid an unexpected incident.
With a lot of equipment shifting from serial connectivity to IP based connectivity a lot of protocols which were never designed to be used across IP networks are being encapsulated within IP and in doing so substantially increasing attack surface. This makes now an especially good time to focus effort on this and to understand the attack paths within your environment.
Future Work
In future articles we’ll delve deeper into some of the techniques and technology we have used in protecting such environments (both things that were and were not effective). We’ll also look at Microsoft Defender for IoT and if and how this fits into defenses.
If you wish to be notified when we publish content then you can follow our RSS feed, or add yourself to our email list:
References
Ransomware attacks hit European facilities:
https://www.thestack.technology/cyber-attacks-european-terminals-sea-invest-evos/
Canadian Centre for Cyber Security - The Cyber Threat to Canada’s Oil and Gas Sector:
https://www.cyber.gc.ca/sites/default/files/cyber-threat-oil-gas-e.pdf
German newspaper Handelsblatt, who obtained the internal BSI report identifying BlackCat as being behind the OilTanking incident:
CISA Director Jen Easterly discussing state sponsored cyber activity – components of this were repeated later at the DefCon 2023 conference:
CISA Advisory on Rockwell PLC vulnerabilities:
https://www.cisa.gov/news-events/ics-advisories/icsa-23-193-01
Rockwell Automation advisory on the vulnerabilities discussed in this article (requires account/registration):
https://rockwellautomation.custhelp.com/app/answers/answer_view/a_id/1140010
Iran’s APT33 potentially exploring cyber attacks on critical infrastructure:
https://www.wired.com/story/iran-apt33-industrial-control-systems/