2024’s AiTM Activity In Numbers
Overview
At Lab539, we’ve developed some unique methods for identifying and tracking Adversary-in-The-Middle (AiTM) infrastructure. We’ve been doing this for a while, so we thought it’d be interesting to reflect on the trends we observed throughout 2024.
Our approach is to actively hunt down backend infrastructure rather than passively collecting data. This post is a summary of what we’ve discovered — it’s not based on campaigns that targeted our customers, aggregated threat feeds, or phishing emails. We’re entirely agnostic to how the AiTM attack occurs. The only infrastructure included here is confirmed AiTM-capable infrastructure; phishing infrastructure isn’t counted unless it meets that threshold (which the majority still does not).
Some of the infrastructure we identify is clearly set up to target a single organisation, while others are part of large-scale campaigns hitting thousands of victims. We treat both the same. While certain indicators allow us to speculate on a campaign’s reach, we rarely get a complete picture of its full scale.
For those not subscribed to our AiTM feed here is a real record for a campaign we saw appear whilst writing this blog post.
{
"hostname": "googletagmanager.mail.loginyah00.com",
"domain": "loginyah00.com.",
"ip": "209.38.232.214",
"rdns": "",
"asn": "AS14061 DigitalOcean, LLC",
"frontend": true,
"backend": true,
"active": true,
"timestamp": 1739263105,
"detected": 1739263105,
"confidence": "high",
"country": "DE",
"eventid": "2f076c59-505a-49f0-9c1f-a1ca7f08ab0e"
},
This is a good representation of the data we are working with, thousands of these records collected throughout the year. When we uncover infrastructure we do our best to populate as many of the fields as possible. The majority of our records will include a domain so we’ve treated the “domain+IP” address combination as the identifier or a unique record for the purposes of these stats. It means that AiTM campaigns that utilise multiple subdomains do not amplify stats (as for the most part they are part of the same campaign). We have had to make allowances for and cleanse data when pulling these together, not least because our detection capability has enhanced throughout the year but also because certain data points are not always available. During analysis for this blog post we have enriched some data further but this was not always possible.
Activity Trends During 2024
Let’s start with a quick look at how we’ve seen campaigns distributed across the year:
After the surge in January 2024, followed by a steep drop in February, the trendline shows a steady increase throughout the rest of the year. July saw the highest level of AiTM infrastructure, though October and November were also significant. We did see things tail off a little in December. However, January stood out the most. We were operating in beta during the first half of 2024, and that did impact some of February’s results as our collection was very intermittent during the month. Even excluding February, the drop after January 2024 was striking, especially since March and April used the same collection techniques without the interruptions seen in February.
Writing this in early February 2025, we reviewed our stats to see if January 2024 was an outlier. It wasn’t. January 2025 has already seen a massive spike in AiTM infrastructure — up over 30% from July (the busiest month of 2024) and a 50% year-on-year increase from January 2024. For whatever reason, January appears to be a peak month for AiTM attacks. We can't directly compare February yet, but early signs suggest AiTM attacks will be even more widespread in 2025.
We use percentages throughout since our dataset isn't always fully populated and this ensures consistency in comparisons. However, to give a point of reference, we now see in excess of 1000 domains per month being used to host AiTM infrastructure, and for each domain we usually see multiple subdomains. The number of attacks, victims, and supporting phishing infrastructure will far exceed this. While some infrastructure is deployed for a single target, most is built for mass attacks, likely reaching thousands of targets and victims. It's fair to say AiTM is now a core tool for many adversaries.
Activity by Time and Date
To try and better understand our adversaries and their operation we decided to delve into our data and look at when we are seeing infrastructure deployed.
We see a peak at the start of the workweek, followed by a noticeable drop over the weekend. Whether this suggests adversaries follow a 9-to-5 schedule or simply operate when their targets are active remains unclear. To dig deeper, we examined time zones to see if there’s a preferred time of day for their activity.
When we look at the hours of operation, we see that most activity occurs between 12:00 and 22:00 UTC, which aligns with the working day in the Americas. On the flip side, the quietest period is around 05:00 UTC — lunchtime across much of the Asia-Pacific region.
We’re undecided on what this truly reveals. One argument is that threat actors targeting victims in New York, for example, might work similar hours to their targets, leading to infrastructure activity that mirrors the New York workday. However, what we’re detecting is infrastructure being deployed — not lures being sent via phishing, smishing, or other means. While lures are likely timed to align with victims' working hours, setting up infrastructure doesn’t necessarily have to follow the same pattern… unless adversaries want to monitor responses and debug issues in real time.
We don’t track when lures are sent, so while we know when infrastructure is deployed, we lack precise data on when victims are actually targeted—something that would be interesting to analyse in the future.
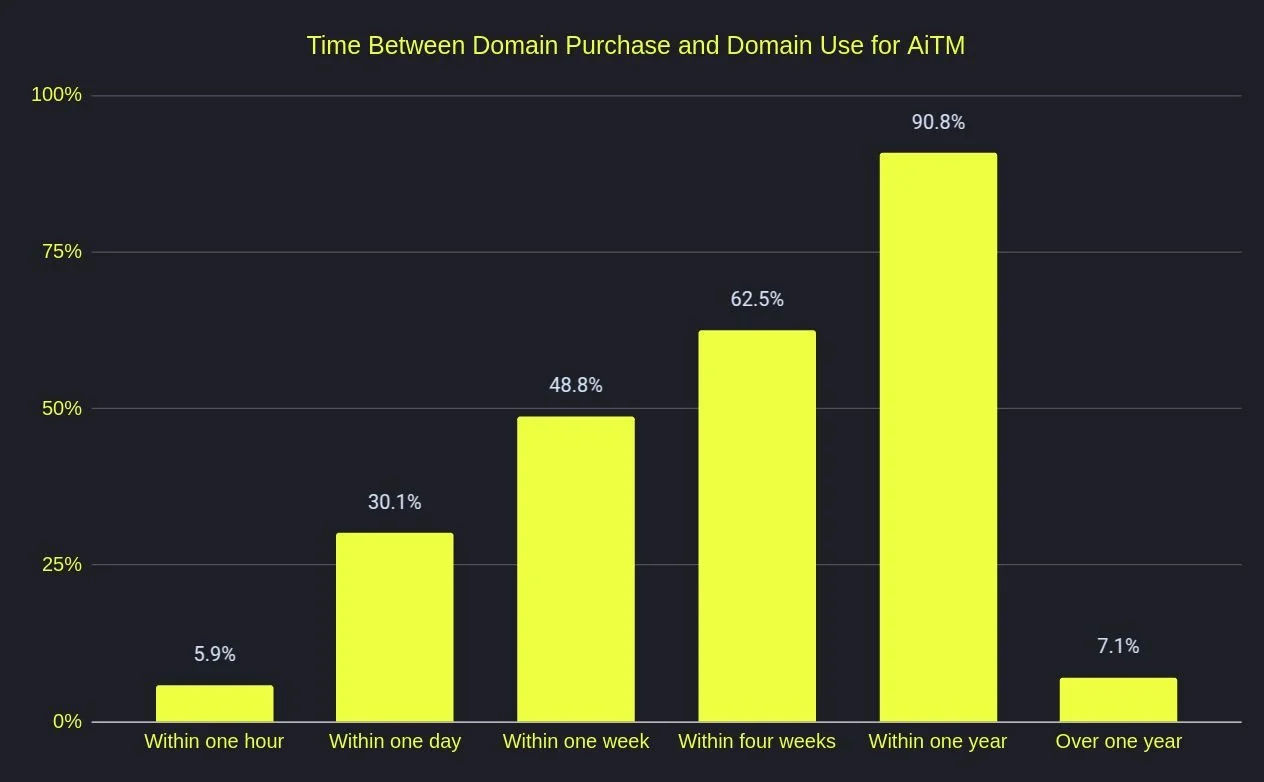
Time to Deployment
One piece of timing information we have computed, is how long it is between a domain being registered and seeing infrastructure being spun up relating to that domain.
We see almost all AiTM domains being used within a year with most being used within a month. If we’re honest, we expected more domains to be used even earlier. We thought the ‘within one week’ category would exceed 70%, but that wasn’t the case. It very much feels like domains are disposable — grab one, use it, burn it, move on. So, it was surprising to see most remained unused a week after registration.
That said, some operators did act fast. The shortest time from registration to use in AiTM infrastructure in 2024 was just 262 seconds — barely over four minutes. We also examined domains used within an hour of registration to see if an automated AiTM service was behind them, but found no clear correlation.
The two oldest domains we observed in 2024 were outliers. One, it.com, sells subdomains of itself, several of which were used for AiTM, but this isn’t a domain that exists solely for AiTM purposes. The other, ibm.net, belongs to IBM and was used for AiTM purposes on several subdomains — likely for testing, based on the hostnames.
Excluding those, the oldest domain actively conducting AiTM operations in 2024 was registered in 2001. Originally tied to a real estate related company, it changed hands in 2016 and again in 2019. The new owner falsely claimed to be the original registrant, clearly knowing what they were doing. We saw activity in 2023, then in 2024 its nameservers moved to Cloudflare. A couple of weeks later, it was being used for AiTM attacks.
This adversary put serious thought into their approach — far more planning than we typically see. Either they were laser-focused on a specific sector, or it was a red team operation.
While a determined adversary or capable red team can bypass simple heuristics, the old rule of thumb still mostly holds: ‘Lower trust for newly registered domains.’ If you blocked all domains registered in the last year, you’d stop over 90% of AiTM infrastructure (along with plenty of legitimate domains, of course! So, whilst not a sensible model to adopt, probably not one to drop from your security weightings).
AiTM Providers of Choice
In previous posts we shared a bit of information about where we see AiTM infrastructure being hosted, so here we reflect on what we saw in 2024 and how, or if, that has changed at all. Here is the top 10 AiTM hosting providers for 2024:
In 2024, we observed AiTM infrastructure hosted across 222 different providers. The top 10 providers have their own section in the chart with ‘Other’ covering the remaining 212.
DigitalOcean held onto its crown from previous analyses as the preferred hosting provider for adversaries carrying out AiTM attacks, starting the year strong and maintaining momentum throughout. We significantly improved our Cloudflare detections in the second half of the year, and while we considered only showing data from that period, it still wouldn’t have impacted first place. However, it would have pushed AWS down to third, with Cloudflare taking silver. That puts Cloudflare in a strong position for 2025 — maybe DigitalOcean finally gets dethroned… or maybe Cloudflare’s lack of cryptocurrency payment options keeps it in second place for a while longer.
A growing trend we’ve seen is that AiTM infrastructure is increasingly not directly referenced in lures (phishing, smishing, etc.). Instead, attackers use trusted sites to pull users in, then employ a series of redirects to their backend AiTM infrastructure. This likely helps evade some URL scanning detections and makes the infrastructure harder to discover. Users are now more accustomed to being redirected to a login page, especially when accessing shared documents, and if they arrive via a site they trust, they’re more likely to trust the final destination too.
As for preferred hosting locations, it’s no surprise that the USA ranks first. This is almost certainly due to major cloud providers defaulting to US-based hosting rather than any adversary preference.
In total we saw hosting across 68 different countries throughout 2024. Canada, Singapore and France trailed Australia on remarkably similar numbers, before things dropped off more radically for the remaining countries.
We wrap things up with a look at which registrars are most preferred by the adversaries. Previously Namecheap held that crown and, yeah, nothing has changed. Namecheap still absolutely dominate as the registrar of choice for adversaries carrying out AiTM attacks.
No doubt the cryptocurrency payment options have played a part in some of the registrars appearing in this top 5. So in all nothing radical on the registrar front in comparison to previous analysis. We’d expected a bit more of a dent from Cloudflare, it’s not like they didn’t appear, but they seem top be much more preferred by adversaries as a DNS hosting provider than are as a registrar.
Summary
Rather than drawing firm conclusions, we've shared the data to provide insight. If we were to make predictions for 2025 it would be a year of increased AiTM activity, with greater reliance on the trust afforded to legitimate services in order to deliver lures without over exposing back-end infrastructure.
Throughout 2024 we have seen increased sophistication in AiTM deployments, with proxy networks and VPNs increasingly being used in order to tunnel authentication while maintaining greater anonymity, and we do expect these type of obfuscation techniques to continue.
Most of the activity we’ve seen in 2024 appears to be indiscriminate account compromise - campaigns where any Google/Microsoft/Other account is of interest. Identity providers remain primary impersonation targets, yet they often offer little help in addressing the issue. Defenders shouldn't have to rely on 'creative' CSS tricks to detect anomalies, nor should non-technical users have to struggle to verify they're on a legitimate identity provider login page. We know that MFA will definitely help here, but with many organisations having gone on the journey of getting MFA deployed only to be learning that not all MFA is created equal — some widely deployed methods offer no protection against AiTM attacks. There is obviously still a way to go here, but at least there is some momentum.
We’ll do a post at some point soon delving into some detail on some of the campaigns that we are seeing. Document and file sharing remains a major attack vector and is something we have posted on before. Certain attack types remain overlooked by the cybersecurity industry. Alongside document fraud, we see significant advertising and marketplace fraud. In these cases, the victims suffer, but it’s often their banks that foot the bill. The platforms being targeted don’t lose out financially, so they have little incentive to act, while banks — despite bearing the cost — lack control over the platforms to mitigate the issue effectively.
AiTM attacks exist because of the choices we’ve made when designing and deploying technology. They are the direct result of a failure to properly threat model systems at the design stage - the result of building systems resilient to current attacks while ignoring the fact that adversaries adapt.
AiTM emerged because MFA made credential theft less viable. But AiTM works only because the most widely deployed MFA options are weak. Seventeen years ago, I watched a colleague bypass RSA two-factor authentication during an engagement to gain system access. It wasn’t called AiTM back then, but the attack was the same. Nearly two decades later, not much has changed. We deploy MFA to mitigate credential theft, yet we rely on approaches we’ve known for decades are vulnerable — and then act surprised when they are bypassed.
With widespread SaaS adoption, we have even less control over how we handle authentication and security. We’re at the mercy of vendor offerings, which is frustrating when effective solutions to these challenges have existed for years.
This inability to apply context-centric security plays a huge role. Major vendors push solutions for the problems they sell products for, leading us to focus on mass-market challenges rather than our own specific risks. In fairness, some of those challenges do apply to us — but are they the ones we actually need to solve? Are they our priority?
We often spend money defending against attack paths that either don’t exist for us or don’t truly impact our organisation. Meanwhile, platform constraints prevent us from tailoring defences to our real-world threats. The result? A constant cycle of incremental “general security” improvements — while adversaries iterate and adapt much faster than we do.
AiTM shouldn’t have been a thing. And yet, here we are.
Webinar
If you’ve found this interesting and would like to hear more about some of our AiTM related activities, then do join us for our webinar which is scheduled towards the end of February 2024.
If you’d like us to keep in touch with future work then tick the box on the form below for updates and maybe drop us a message too.